The Discovery Protocol
Security, Workflows, and Fixed-Price Scoping
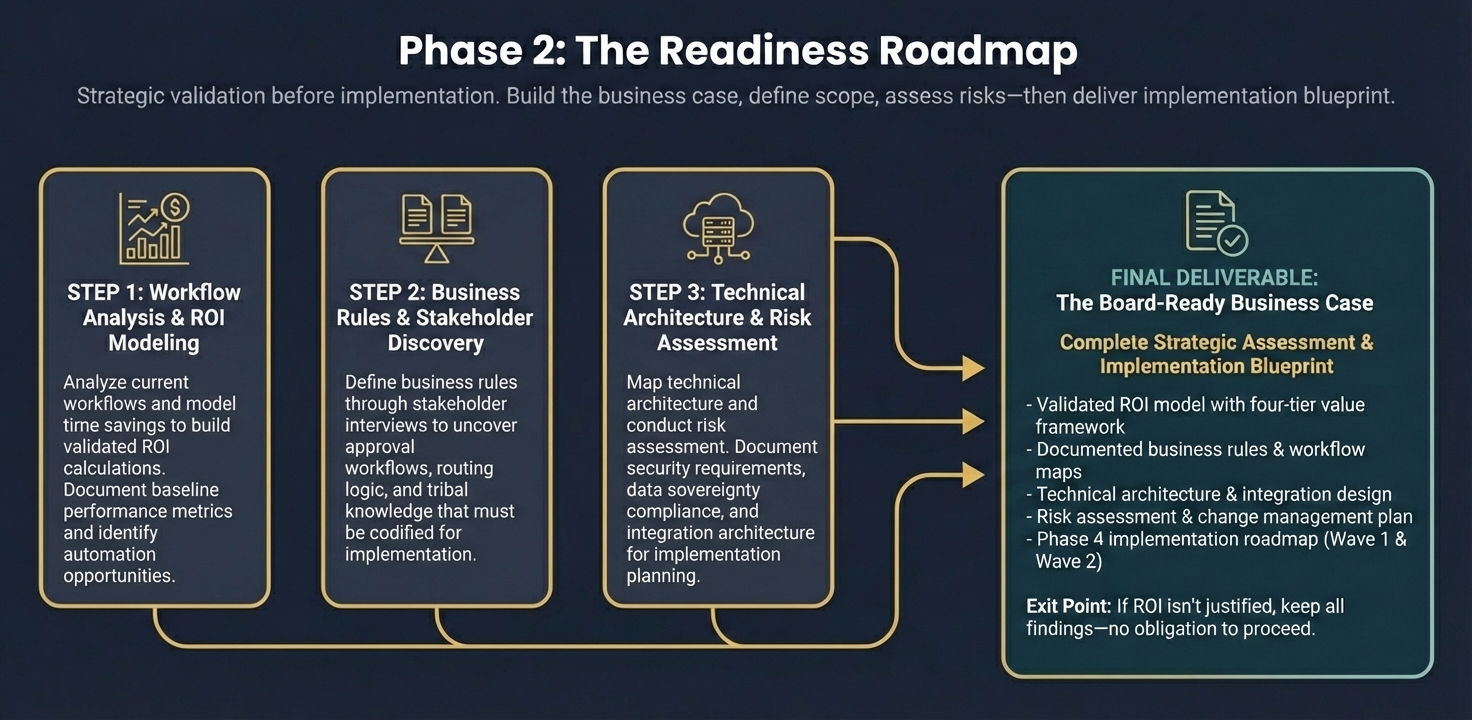
Phase 2 isn't a strategy meeting—it's an active engineering investigation. We audit your Azure/AWS infrastructure, conduct stakeholder interviews to map workflows, and codify business rules before locking the implementation price.